Strengthening Blockchain Security: Best Practices and Mitigating Common Threats
May 20, 2025
Strengthening Blockchain Security: Best Practices and Mitigating Common Threats
Blockchain and Web3 apps are shaking up industries, bringing new levels of openness and decentralization. But as we push boundaries, we face risks: hackers are always looking for weak spots to exploit. In 2024, Chainalysis tells us that hackers stole about $2.2 billion in blockchain-related attacks – that’s 21% more than in 2023. Shady dealings on blockchains have ballooned ($51.3B went through dodgy addresses in 2024), which shows that keeping blockchains safe is now a big deal for businesses. Companies, startups, and go-getters need to use strong blockchain safety tricks and get ahead of threats to keep assets and user trust safe. This deep look examines today’s threat scene, spots common weak points, and lays out tried-and-true plans – from checking smart contracts to using multi-signature wallets – to secure decentralized systems. Throughout, we point out how expert blockchain development partners like Blockchaintechs.io can help teams put these defenses in place.
Blockchains are not invulnerable to attack; rather, the larger the adoption, the greater the incentive for cybercriminals. Chainalysis estimated in 2024 that criminal crypto flows were $40.9 billion (at least) – approximately $51.3B including probable undiscovered funds. The upsurge illustrates how each additional protocol, smart contract, and user contributes to the decentralized network’s attack surface. Even while some types of fraud fell (Chainalysis reported overall scams dropped in early 2024), more advanced threats such as ransomware are on the rebound – one report demonstrated ransom-related crypto thefts rose 62% in 2023. Briefly, new Web3 projects need to take web3 security as seriously as they would traditional IT security. Companies planning to develop or release Web3 products should design security from day one. Top blockchain builders and consultants, like Blockchaintechs.io, highlight a security-first approach: incorporating multi-layer defenses and code audits into the development process. Through this, projects can sidestep the expensive missteps in high-profile exploits.
Need Custom Blockchain Solutions?
From DeFi apps to DAO governance platforms, we build future-ready decentralized applications tailored to your business needs.
The Rising Threat Landscape for Blockchain
Blockchain networks have shown resilience in certain areas – public chains are open-source and heavily scrutinized – but attackers consistently find new ways to crack smart contracts, s teal wallets, or take advantage of operational mistakes. Important trends over recent years highlight why vigilance is important:
1. Surging Hack and Theft Activity: Crypto hacks have reached new heights. Chainalysis statistics (2015–2024) indicate annual peaks in 2021–2022 (~$3.3–3.7B each) and also significant losses in 2024. 2024 alone reported 303 hack events (compared to 282 in 2023) with $2.2B stolen.
2. Although a few of the high-dollar heists (such as some bridge hacks) dwindled later in 2024, the rate of attacks is growing. As an example, the number of hacks increased 303 in 2024 from 282 in 2023, so 2024 became the most hacked year ever. This trend indicates that attackers are becoming progressively bolder and more plentiful.
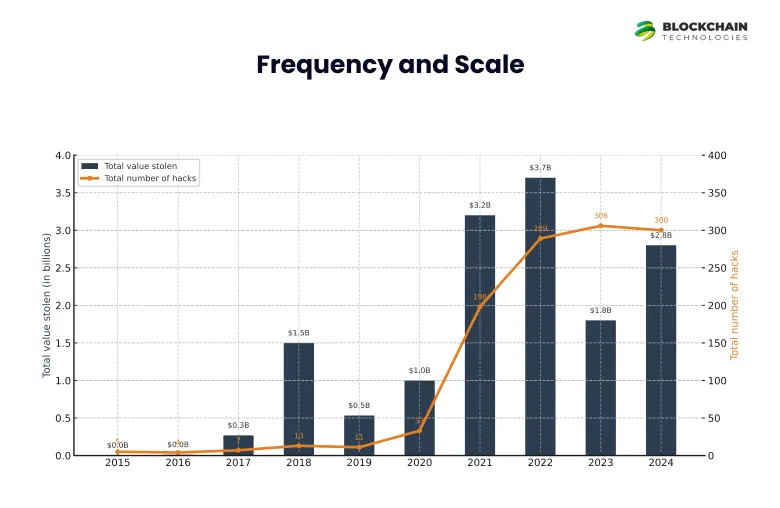
3. Changing Targets: The targets of the attacked platforms have evolved over time. In 2021–2022, DeFi protocols were the primary target. As of mid-2024, however, centralized exchanges and custodial services came to dominate the losses. Chainalysis points out that hacks on centralized platforms (such as a $305M DMM Bitcoin hack and $234.9M WazirX hack in 2024) propelled much of the year’s theft. The chart below shows stolen funds by platform category (DeFi vs. centralized, etc.) across recent quarters.
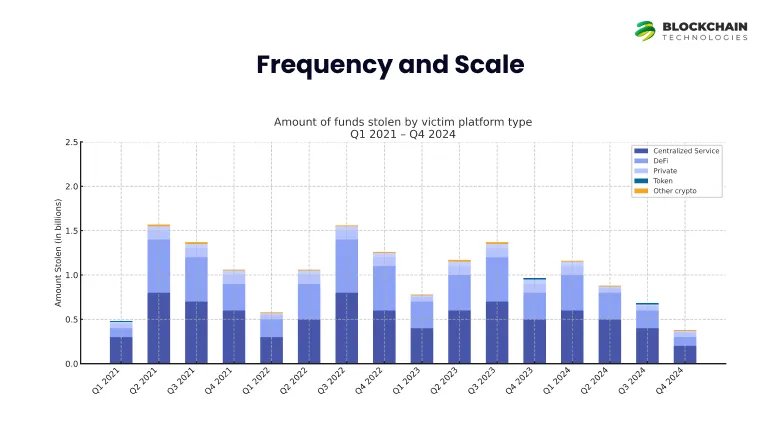
4. DeFi Shifts: In early 2024, DeFi remained having the most dominant share, but in mid-2024’s biggest heists, they hit exchanges. Offenders usually tread where wealth accumulates. Centralized services (custodians, exchanges) now control immense user money, so private key exploits there can bring immense spoils
5. Private key compromises: Throughout all hacks in 2024, the most prevalent failure was private key compromise. Approximately 43.8% of crypto stolen was through key or account attacks. This also included situations where developers or operators handled keys improperly, such as in the DMM hack, which is suspected to have been due to poor key security. Halborn’s analysis reaffirms that compromised accounts (most often through stolen private keys) represented 80%+ value lost in 2024 attacks
6. Advanced Techniques: Contending techniques nowadays stretch from the complex to the opportunistic. Smart contract vulnerabilities (e.g., reentrancy flaws or unguarded calls) bleed pools dry, flash loans enable attacks with borrowed capital, and even social engineering or phishing schemes can be used to deceive admins into sending assets. Crypto ransomware-style extortion is also on the scene: attackers often steal coins and later request payment in exchange for their return or desistance from blockchain disruption. In 2023, crypto ransom payments jumped dramatically while other theft declined.
These trends illustrate that threats are complex. Security teams need to think holistically: securing on-chain code isn’t enough; teams need to defend keys, infrastructure, and even user habits. The attack surface includes smart contracts, nodes, wallets, oracles, bridges, and applications.
Common Blockchain Security Threats
Since there are so many different types of attacks, it is useful to group the most typical threats. Web3 security specialists recognize a number of categories of vulnerabilities which are often the cause of incidents:
- Private Key Theft / Credential Compromise: As mentioned, stealing a user or admin’s private key is an “attackers’ golden ticket”. Methods include phishing (malicious dApp interactions, phishing airdrops, email phishing) and malware on the users’ devices. Social engineering may be used to deceive developers or users into divulging seeds or performing harmful transactions. With a private key, an attacker can legally authorize transfers out of any corresponding account. This attack highlights the demand for sound crypto wallet protection (hardware wallets, safe keystores, multi-signature backups) and end-user training.
- Smart Contract Vulnerabilities: Code bugs in contracts can cause direct losses. Eg, famous ones are reentrancy (a contract calls another contract that re-enters the former function before state is updated) and integer overflow/underflow (arithmetic failures that reverse balances). OWASP’s Smart Contract Top 10 (2025 edition) includes many such vulnerabilities: Access Control flaws, Price Oracle Manipulation, Logic Errors, Unchecked External Calls, Reentrancy, Flash Loan Attacks, Integer Over/Underflow, etc. The DAO hack (2016) is the quintessential reentrancy example. For instance, unbounded external calls (SC06) can destroy logic if the called contract reverts. Integer overflows (SC08) can allow attackers to wrap balances. These issues usually hide in complicated DeFi protocols, NFT contracts, or any bespoke on-chain logic.
- Flash Loan and DeFi Attacks: Flash loan-enabled DeFi protocols (unsecured loans that only live within a single transaction) are vulnerable to manipulative exploits. An attacker can take out a massive loan, manipulate an oracle or liquidity pool, and then repay the loan – harvesting arbitrage profit in one block. Euler Finance is a recent case in point: in March 2023 it was hit by a $197M flash loan attack when a missing check permitted funds to be drained. Other protocols such as dForce and Platypus also encountered flash loan attacks in 2023. DeFi security standards (see below) seek to avoid these using time delays, liquidity constraints, and oracle protections.
- Oracle and Data Manipulation: Most contracts depend on external data (price feeds, randomness). If an attacker can manipulate these inputs, they can induce bad contract behavior. OWASP mentions Price Oracle Manipulation (SC02) as a high-risk threat. For example, by price feed spoofing, a hacker could deceive a lending platform into selling collateral at a low price, then buying it back. De-centralized oracle networks (Chainlink, Band) and using multiple data sources can help counteract this.
- Bridge and Cross-Chain Attacks: Cross-chain bridges (which exchange assets between blockchains) have been profitable targets. These tend to need “guardians” or multi-sig to approve cross-chain transfers. If those keys get stolen, or if buggy code allows an attacker to mimic a legitimate request, enormous theft is possible (e.g. Ronin Bridge’s $615M hack in 2022). Bridges need to be secured by multi-signature governance (see below) and careful audits.
- Denial-of-Service (DoS) and Other Exploits: Other attacks seek to render services unavailable or cause contract failure (e.g. gas exhaustion loops). Though financially distinct from theft, DoS bugs can nonetheless destroy projects. Example: a buggy fallback function leading to inordinate gas consumption and making a contract unusable.
- Social Engineering and Phishing: Beyond bugs in code, there is a dominant human factor. Phishing URLs can be used to trick users into sending attacker wallets tokens. Impersonation of support paths or fake versions of tokens are typical. Wallet UIs in security-aware projects include phishing resistance and user education.
In short, blockchain threat vectors span technical vulnerabilities and operational vulnerabilities. Mitigation involves all these areas by means of a holistic security plan.
Secure Your Smart Contracts Before They Go Live
Don’t leave your Web3 project vulnerable to reentrancy, flash loan exploits, or logic flaws. Our expert team performs rigorous smart contract audits using automated tools and manual review.
Smart Contract Vulnerabilities and Exploits
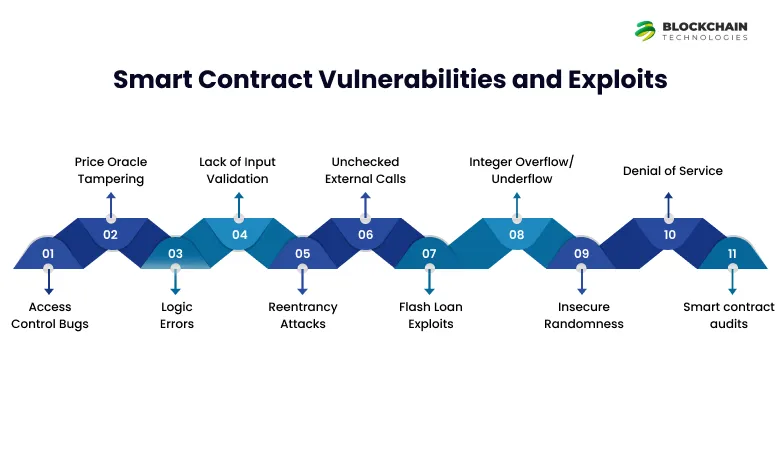
Smart contracts manage on-chain business logic so their bugs often cause direct losses. Here are some main smart contract weaknesses to look out for, based on industry surveys and OWASP’s newest list:
- Access Control Bugs (SC01): Contracts need to control who can do what. A missing onlyOwner check or set modifier can allow anyone to call special functions (such as creating tokens or taking out funds). Making sure require conditions are right is key.
- Price Oracle Tampering (SC02): If a contract depends on just one data source (or centralized oracle), someone can mess with that feed. Using decentralized oracle networks and reality checks is essential.
- Logic Errors (SC03): Correct syntax doesn’t guarantee intended behavior. Bugs in business logic—like wrong interest calculations or flawed token distribution—can drain value without any external hack. Thorough testing and code reviews help spot these issues.
- Lack of Input Validation (SC04): Functions that take external input must check it. For instance, a token swap function should verify that token addresses are valid or that amounts make sense. Without this, attackers can send malicious data or trigger unusual bugs.
- Reentrancy Attacks (SC05): This well-known bug occurs when a contract sends out money (to a recipient) before updating its own balances. The recipient contract can then call back (“re-enter”) the sender’s function multiple times emptying funds before the state gets updated. The DAO hack stands out as the classic example. Up-to-date Solidity safeguards (like checks-effects-interactions pattern or reentrancy guards) play a key role to prevent this.
- Unchecked External Calls (SC06): When a contract calls an outside contract, it must check if the call worked. If not checked even a revert in the called contract can leave the caller’s state inconsistent. Always handle return values and reverts.
- Flash Loan Exploits (SC07): When your contract allows someone to borrow big sums in a single transaction (flash loans), make sure attackers can’t abuse the logic with these sudden large balances. Many hacks in 2022–23 involved flash loans to boost values and empty liquidity pools.
- Integer Overflow/Underflow (SC08): In earlier Solidity versions, math operations could wrap around. For instance, taking 1 from 0 results in a massive number. Though Solidity 0.8+ checks this by default, you should still look at any math operations (and use SafeMath or built-in checks). OWASP continues to rank this among its top 10 issues.
- Insecure Randomness (SC09): On-chain randomness poses challenges. Using blockhash or timestamp for random number generation can leave systems open to attacks. For crucial random needs, it’s best to use well-tested VRF oracles.
- Denial of Service (SC10): Functions can run out of gas when they loop over arrays without limits or write to storage too much. Bad actors might flood the system with transactions to trigger these gas limits and shut down functions. To protect against this, developers can build in circuit breakers or make systems pausable.
- Smart contract audits are a must because these weaknesses can be hard to spot. A team of expert Smart contract auditors will check code for the issues mentioned above. A recent guide points out, “Regular audits are vital since smart contract flaws can cause big losses”. Tools like Slither and MythX help with manual checks by finding common patterns. Many companies also start bug bounty programs to get the community involved in finding issues.
Case Study: Euler Finance, an open lending protocol, lost about $197 million to a hack in March 2023. The attacker borrowed money to change interest rates and steal assets. This shows that even well-known DeFi platforms can have weak spots if they don’t plan for every case. It proves the need for code safeguards (like checks to ensure “liquidity is available”) and multiple signatures for admin tasks.
Smart contract security goes hand in hand with DeFi security. DeFi projects should set limits (like the biggest loan size), use oracles on multiple chains, and add time delays to governance (so the community can react to changes). Always think that public open protocols will face attacks – plan with this in mind.
Decentralized Application (DApp) Security
Smart contracts aren’t the only part of decentralized applications (dApps) that need protection. Web apps mobile apps, and backend services that connect to the blockchain also require safeguarding:
- Key Management in Front-Ends: Most dApps depend on user wallets like MetaMask or WalletConnect. For high-stakes actions, push users to link hardware wallets such as Ledger or Trezor. Make sure your interface displays transaction details and alerts users about signing unfamiliar data. To prevent phishing, host your dApp on HTTPS with HSTS and teach users to check URLs.
- Secure Backends: If your dApp uses off-chain servers (for example, to gather data, handle APIs, or execute off-chain business logic), put standard web security measures into action (SSL/TLS, firewalls, intrusion detection). Keep API keys safe and never show secrets in the frontend code.
- Multi-Signature Authorization: One of the best ways to keep decentralized applications safe through multi-signature wallets is to ask for more than one approval for key operations. Take your dApp’s admin treasury (like DAO funds staking pools, or upgrade ability) as an example. You should keep these funds in a multi-sig wallet (like Gnosis Safe) that needs 2-of-3 or 3-of-5 keys. This setup stops a single bad developer or hacked key from moving funds on their own. Multi-sig wallets add an extra layer of safety. Investopedia points out that they “lower the risk of digital asset theft that relies on a password or wallet key”. For DAO governance and dApp upgrades multi-sig (or multi-party MPC) setups have built-in approvals, which cuts down risk by a lot.
- DApp-Specific Audit and Testing: Many teams still check only their smart contracts and ignore the user interface. However cross-chain bridges and wallets often have complex UX flows that bad actors can exploit (e.g. transaction cryptojacking through hidden signatures). Run security tests on your whole stack. Threat modeling static analysis of the frontend (to catch XSS, for example), and penetration tests can reveal problems in smart contract callers, websocket connections, and other off-chain logic.
- Web3 Security Best Practices: Make sure you update all libraries and dependencies – for instance, if you use an SDK to connect to Ethereum, stick to the newest secure version. Instead of creating your own abstractions, go for proven frameworks (like OpenZeppelin contracts). Put your dApp through its paces under heavy loads and check that your nodes/hosts can manage large amounts of RPC traffic.
Web3’s decentralized structure means you can’t just install a quick fix from a main server for contracts already out there. Once something goes wrong on the blockchain, you often can’t undo it. That’s why it’s so important to build in solid safeguards (like multi-signature wallets, ways to pause things, and thorough testing) when it comes to keeping decentralized apps secure.
Best Practices and Mitigation Strategies
Given these threats, what can projects do to be proactive? The aim is to reduce blockchain security risks through multiple layers of defense. Here are key strategies and best practices:
- Conduct Regular Audits (Blockchain Audit & Smart Contract Audit): Get experts to check your code and setup before you launch and after big changes. A blockchain audit needs to look at smart contracts how nodes are set up, who can access what, and even the rules for working together. Companies that specialize in this (or skilled teams in your company) use both computer programs and people to review everything. For the most important contracts, you can use a method called formal verification. One Web3 guide says, “problems in smart contracts can cause big losses so you need to check them often”. After the audit, do something about everything they find. Fix the code, change settings, and test again.
- Put Multi-Signature and Multi-Party Controls in Place: As mentioned using multiple keys for any sensitive task cuts down risk. This covers multi-sig for treasury wallets multi-party computation (MPC) to manage custodial keys, and time-lock delays when upgrading contracts. For instance, a 48-hour timelock on DAO actions makes sure the community can step in if a proposal looks harmful. A specific way to ensure security in decentralized apps through multi-signature wallets is this: every high-value transaction needs approval from an independent party or committee.
- Boost Key and Wallet Protection: Guard private keys and wallets at every level. Store keys offline with hardware wallets. Companies should use Hardware Security Modules (HSMs) or multi-sig vaults instead of giving single developers key control. Use multi-factor authentication (MFA) for any web services or custodial accounts. Back up mnemonic seeds safely (never in the cloud or email). In other words apply top-notch crypto wallet security: approved people get access, and always to the bare minimum. This tackles the huge portion of theft that key breaches cause.
- Use DeFi Security Methods: If you’re starting any financial protocol:
- Timelocks: These cause a delay in crucial changes. When someone suggests a contract update or big withdrawal, a built-in wait period allows time to review or stop things if needed.
- Liquidity and Rate Limits: These put limits on how much can move or be borrowed at once. For example, they cap flash loan sizes or pool withdrawals to make big exploits tougher.
- Trusted Oracles and Price Feeds: These rely on decentralized oracle networks and need multiple data sources. They protect against Price Oracle Manipulation by checking if prices make sense (like limiting price changes per block).
- Insurance and Audits: These involve getting coverage or setting up backup funds to pay back users if an attack happens (common in DeFi insurance protocols). They also mean keeping finances open to view.
- Secure Development Lifecycle: Mix security with DevOps. Use version control with guarded branches, ask for code checks and team coding for all updates, and add ongoing integration (CI) tools that do static checks (like Slither MythX) on every change. Teach your dev team about safe coding rules. Stick to smart contract safety best steps like using proven libraries (OpenZeppelin) cutting down on-chain storage, and keeping contracts as basic as you can. Switch keys often and check system records for odd things.
- Real-Time Monitoring and Analytics: Tools like blockchain analytics and behavioral monitoring catch suspicious activity fast. Chainalysis’s Hexagate offers real-time threat intelligence and flags high-risk addresses. Likewise tracking contract metrics (sudden jumps in transactions, gas usage, or token movements) can set off alarms. Active monitoring plays a crucial role to stop attacks . As Chainalysis points out, “real-time blockchain analytics and tools […] are helping teams detect and stop attacks before they occur”. Put money into dashboards that keep an eye on both on-chain and off-chain signals.
- Incident Response Planning: Get ready for the unexpected with a solid incident response plan. Set up clear steps to freeze contracts (if you can) change keys, and talk to users. Acting fast and can reduce harm and keep people’s trust.
- Collaboration and Community: Everyone shares the job of staying secure. Team up with the community and security experts. Run bug bounties on platforms like Immunefi. Share what you learn from any problems and help with research (like the OWASP SCS Top 10 open standards). Learn from others – for example, Chainalysis and SlowMist put out yearly security reports that show new trends.
- Building Security-Aware Teams: , make sure your team prioritizes security. This involves bringing on board or seeking advice from blockchain security specialists. If your internal team lacks extensive knowledge in smart contract security or blockchain audit methods, think about partnerships. Getting skilled blockchain developers and auditors on board can lower risk. Experienced blockchain engineers will create secure structures from the start instead of adding fixes after the launch. For example, bringing in experts to audit smart contracts can spot subtle logic problems that non-specialists might overlook.
- Free Blockchain Security Consultation: Teams that don’t know where to begin should seek expert advice. At Blockchaintechs.io, we provide a free Blockchain security consultation to check your setup and methods. Our experts will spot weak areas (from storing keys to contract logic) and suggest custom ways to reduce blockchain threats. Get in touch with us for a free security review and receive practical tip
Boosting Security in Decentralized Apps with Multi-Signature Wallets
Multi-signature key management stands out as a strong approach that deserves its own spotlight. Multi-signature wallets help to make decentralized applications more secure eliminating single failure points. Here’s the lowdown:
- N-of-M Signing: Set up wallets so that N out of M approved keys need to sign any transaction. Take a 2-of-3 multi-sig setup as an example. It means two team members must give the green light for transfers. This setup means that even if someone hacks or steals one key, they can’t move funds by themselves. In real-world use many DAOs and dApp admin teams opt for 3-of-5 or 4-of-6 setups to beef up security.
- Hardware Key Vaults: Hardware wallets play a role in the multi-sig setup. Different key storage methods (Ledger, Trezor, YubiKey, etc.) work together to prevent all keys from ending up on a single device. Some systems even use multi-party computation (MPC) to ensure no single machine ever holds the complete key.
- Geographical and Role Separation: Signers spread out across locations and roles. For example, one key might be on an executive’s hardware wallet another on a security officer’s, and a third on a cold HSM in the company vault. Incidents like the Parity multi-sig bug (where a single library error froze funds) teach us not to rely on just one person. Multi-sig makes teamwork necessary.
- Emergency Recovery: Multi-sig can fail if people lose keys. You need to plan to recover (e.g. a key sharding/backup plan that’s secure). Many multi-sig setups include an emergency “safeguard” time where transactions wait letting an emergency key step in.
Investopedia backs this up: multi-sig wallets “make crypto assets safer” by needing more than one person to approve a transaction. For any decentralized app that holds user money, using multi-sig is one of the easiest ways to put web3 security best practices for wallets into action. It connects to bigger blockchain safety efforts by making even strong attacks (like stealing private keys) much harder to pull off .
Need Help with Blockchain Strategy? Let's Talk
Book a 30-min free strategy session with our Web3 consultants. From choosing the right blockchain to planning MVP features, we’ll guide you.
Crypto Wallet Security
Very much connected to multi-sig is personal wallet security. All stakeholders — users and developers — must observe strict crypto wallet security practices:
- Use Hardware Wallets: Wherever feasible, keep keys in a hardware wallet (Ledger, Trezor, etc.) instead of on software that may be compromised. Such devices store keys offline. For high-frequency transactions, use “Air-gapped” wallet configurations.
- Enable MFA and Passphrases: Most wallets enable multi-factor and extra passphrases. Even if a key file is lost, a good wallet passphrase provides an extra level of protection.
- Network Hygiene: Keep computers used to manage wallets secure (no malware, latest OS and antivirus). Never reuse addresses across numerous services.
- Education: Educate your staff on phishing (e.g., never click dubious wallet alerts) and test transactions. Conduct security exercises: e.g., practice a suspected account breach and enact response procedures.
Given that nearly half of all crypto stolen includes key abuse, these are core practices. Blockchainsecurity best practices require that funds be transferred only with clear, secure approval — by hardware sign-off, multisig co-signers, or threshold cryptography.
Real-World Examples: Lessons Learned
Studying failed and successful security examples serves to solidify best practices:
- DAO Hack (2016): The quintessential smart contract flaw exploit. The decentralized fund (DAO) suffered from a reentrancy bug which enabled an attacker to withdraw ~$60M. Subsequently, the community hard-forked Ethereum and implemented reentrancy guards as a best practice. Lesson: minor code errors can lead to huge losses.
- Parity Multi-sig Freeze (2017): A library bug in Parity wallet unexpectedly “suicided” the code, freezing around ~$300M worth of ETH in Parity multisig wallets. Though multi-sig was intended for security purposes, this debacle reveals how a robust auditing process must be ensured of your own multi-sig implementation.
- OpenZeppelin Community: On the one hand, the OpenZeppelin team publicly releases audited smart contract libraries reviewed by numerous experts. Numerous Web3 projects reduce risk by constructing on top of these community-reviewed contracts. Using such battle-tested code (for ERC20/ERC721 tokens, Ownable modules, etc.) is an easy “best practice” to not reinvent buggy code.
- Euler Finance (2023): Recall that Euler’s lack of a safety check saw a flash loan attacker make off with $197M. Euler’s recovery (the attacker remitted funds) shows the positive side of community reaction. That said, the moral is one line of lacking code in a loan agreement costing huge amounts. Bug bounties and duplicated checks are used by DeFi projects now all because of it.
- North Korean Hacks: Certain high-profile hacks (Ronin, Axie Ronin Bridge, Harmony) have been attributed to the Lazarus Group. These are generally stolen private keys at high privilege. It highlights that even nation-state actors are aiming at crypto and that sometimes “traditional” precautions (such as keeping keys air-gapped, utilizing HSMs, and multiple signers in different places) are what are between security and disaster.
These examples underscore that blockchain threat mitigation is never one-and-done. It demands constant watching, community education, and frequently third-party monitoring.
Why Blockchaintechs.io is the Proper Partner for Scalable and Secure Blockchain Solutions?
For businesses and startups trying to navigate this intricate security environment, it is vital to partner with mature blockchain security experts. Blockchaintechs.io merges technical knowledge with consulting backgrounds to offer end-to-end secure blockchain solutions. Here’s why we keep your project safe:
- Expert Development Team: Our blockchain engineers are educated in secure coding and architecture. We can integrate your team to design features and have them adhere to the current best practices in blockchain security. Want to enhance your in-house skillset? Think about hiring seasoned blockchain developers at Blockchaintechs.io, who deliver a security-centric design approach, from multi-signature wallets to hardened smart contracts.
- Comprehensive Audits: We provide thorough smart contract audits and full-stack blockchain audits. This involves automated testing and manual code reviews by security engineers. We provide clear reports and remediation recommendations after an audit. You can book a smart contract audit with us to identify vulnerabilities prior to deployment.
- End-to-End Solutions: In addition to code, we also consult on deployment, operation, and monitoring. From deploying secure nodes to incorporating analytics software (such as Chainalysis), we assist architects in deploying sound security infrastructure. Our consultants are familiar with DeFi security protocols and can architect systems with mitigation baked in. Require an end-to-end solution? Contact us to receive a quote for end-to-end blockchain solutions – custom offerings scale to your company size and industry.
- Security Consulting: Not sure where to begin? Leverage our Free Blockchain Security Consultation. We’ll examine your project plan, mark high-risk issues (e.g., missing audits, single points of failure, key management shortfalls), and suggest actionable follow-up steps. This no-hassle consultation can save you time and dollars by focusing on the most essential security enhancements.
Ongoing Partnership & Support: Web3 initiatives change quickly. Security must change with them. Blockchaintechs.io is still a partner after launch, guiding you on upgrades, managing incident response if necessary, and keeping your team informed about new threats.
In each engagement, Blockchaintechs.io focuses on cooperation and teaching. We enable your developers with training in smart contract weakness, DApp security, and new web3 security tools. By joining together early, we embed security within your product roadmap, sidestepping the pricey retrofits they’ve had to endure. Start Today: Be it an enterprise introducing a permissioned blockchain or a DeFi startup, it’s high-stakes. Avoid waiting for there to be a breach to proof your defenses against. Reach out to Blockchaintechs.io today to talk about how we can assist in securing your platform – from smart contract audits to multi-sig wallet configuration, to end-to-end blockchain solutions.
Get a Quick Blockchain App Cost Estimate
Wondering how much your blockchain app will cost? Whether it’s DeFi, NFT marketplace, or a Layer 2 protocol, we’ll break it down for you — fast and free.
Conclusion
Blockchain security is an ever-present obligation. The immutable, decentralized nature of blockchains ensures that errors can’t be reversed. By being aware of the typical threats – from bugs in smart contracts to theft of keys – and taking active steps to apply mitigation techniques, organizations can minimize risk significantly. Key strategies include comprehensive security audits, multi-signature controls, strict key management, and ongoing monitoring.
Enterprises and startups involved in Web3 should adopt these blockchain security best practices as non-negotiables. Given the rapidly evolving threat environment (as recent data shows), there is no room for complacency. Partnering with a trusted security provider like Blockchaintechs.io ensures that you’re building on a foundation of safety. With expert developers, auditors, and consultants on your side, your project will have the robust defenses needed to thrive. Secure your blockchain today: tap into expert skills for auditing, development, and strategy. The benefits – safeguarded assets, user trust, and regulatory peace of mind – far exceed the cost of a breach. With the right team and best practices, your blockchain platform can be both innovative and resilient to the threats of today.
Hire Pre-Vetted Blockchain Developers
Looking for skilled developers who speak Solidity, Rust, or Substrate? We offer dedicated blockchain development teams — ready to build.

