Securing the Future: AI-Enhanced Decentralized Cybersecurity with Blockchain
May 29,2025
In a world where over 2,200 cyberattacks occur each day and data breaches cost an average of $4.45 million, traditional security systems are no longer enough. As cybercriminals evolve, so must our defenses. The next frontier in digital defense lies in the fusion of AI cybersecurity and blockchain security, two technologies revolutionizing how we protect sensitive data and digital infrastructures.
The demand for decentralized cybersecurity with AI solutions powered by AI threat detection and blockchain data protection is soaring, driven by the need for transparent, tamper-proof, and autonomous systems.
- According to a recent report, Global Cost of Cybercrime: By 2025, the global cost of cybercrime is projected to reach $10.5 trillion.
- The average cost of a data breach has risen to $4.88 million globally in 2024, with projections hitting $5 million by 2025.
This blog explores how to use AI and blockchain for cybersecurity and reveals the benefits of decentralized cybersecurity platforms for future-ready enterprises
What is Blockchain Technology and How Does it Work?
Understanding blockchain technology in cybersecurity with AI starts with grasping how this decentralized ledger system fundamentally differs from traditional databases. Here’s a breakdown:
What is Blockchain?
Blockchain is a type of distributed ledger technology (DLT) that records transactions across a network of computers (or nodes), ensuring that the data is secure, transparent, and nearly impossible to alter.
Key Components of Blockchain:
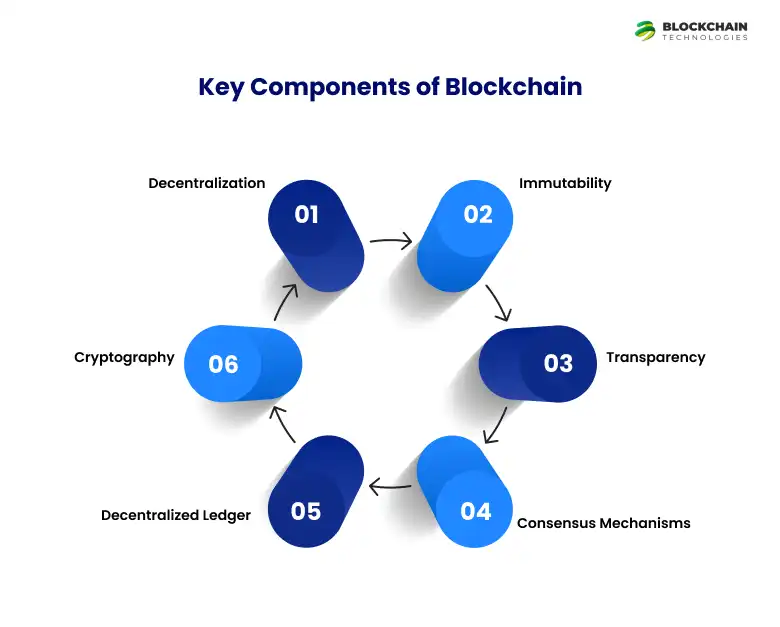
- 1. Decentralization Instead of a single server or authority, data is stored across multiple nodes. This eliminates the risk of a single point of failure, enhancing system resilience.
- 2. Immutability Once information is added to the blockchain, it cannot be changed without consensus. This is ideal for cybersecurity in blockchain applications where data integrity is crucial.
- 3. Transparency All participants in a permissioned blockchain network can view the history of transactions. This fosters trust, especially in enterprise cybersecurity systems.
- 4. Consensus Mechanisms Algorithms like Proof of Work (PoW) or Proof of Stake (PoS) are used to agree on the validity of transactions without a central authority. These ensure only legitimate data is recorded.
- Decentralized Ledger: Blockchain is a distributed and immutable record of transactions, shared across a network of computers. This decentralization eliminates single points of failure and makes it incredibly difficult for malicious actors to tamper with the data.
- Cryptography: Cryptographic hashing and digital signatures secure each block of transactions and link them chronologically, ensuring the integrity and immutability of the chain. Any alteration to a block would change its hash and invalidate all subsequent blocks.
Benefits of Decentralized Cybersecurity Platforms with Blockchain
AI-powered decentralized cybersecurity solutions reduce reliance on centralized control and ensure autonomous threat mitigation. Here’s how this powerful combo reshapes cybersecurity with trust, transparency, and tamper-proof protection:
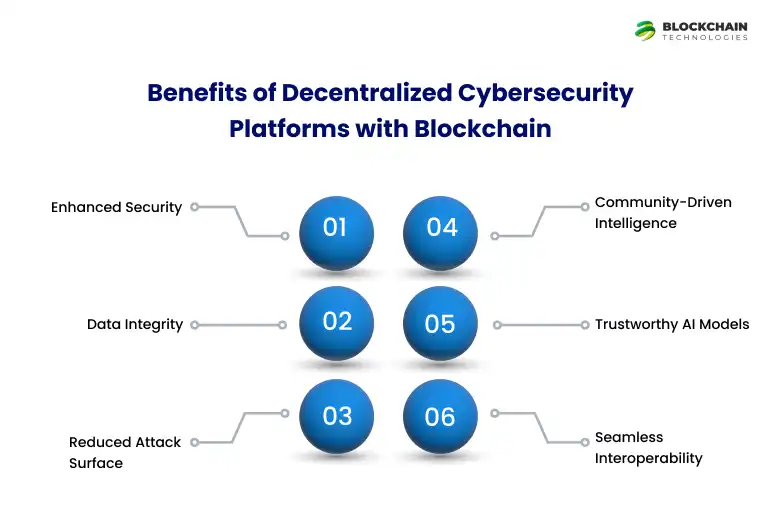
- Enhanced Security Immutable blockchain records meet intelligent threat detection, creating a system that’s nearly impossible to breach.
- Data Integrity With blockchain, every bit of data is verifiable and unalterable, ensuring what’s written stays true.
- Reduced Attack Surface No central servers. No single point of failure. Decentralization distributes risk and strengthens defense.
- Community-Driven Intelligence Harnesses decentralized, crowd-sourced threat data, bringing real-time insights from across the network. Community-driven threat intelligence in blockchain ensures a continuously evolving defense posture.
- Trustworthy AI Models Blockchain logs and verifies every AI-driven decision, offering full transparency and auditability in real time.
- Seamless Interoperability Built to scale across platforms and industries, these systems adapt and secure complex digital environments effortlessly.
Don't Let Cyber Threats Hold You Back!
Unlock the power of decentralized AI cybersecurity, a revolution in protecting your digital world.
How Blockchain Works Step-by-Step: A Technical Walkthrough of Decentralized Transaction Processing
Blockchain is a math, cryptography, and consensus working in harmony. Blockchain’s step-by-step workflow solves the “Byzantine Generals Problem”, how to trust strangers in a distributed network. By combining cryptographic hashing, decentralized consensus, and immutable record-keeping, it creates a system where:
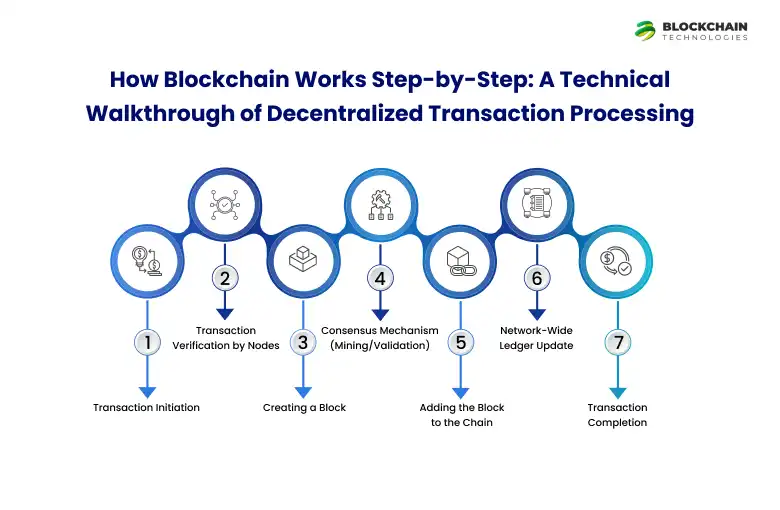
Step 1: Transaction Initiation
- A user initiates an action like sending crypto, signing a contract, or logging medical data.
- The transaction details (sender, receiver, amount, timestamp) are bundled into a data packet.
Transactions are signed with the sender’s private key (a cryptographic password) to prove ownership.
Example: Alice sends Bob 1 BTC. Her wallet uses her private key to “sign” the transaction.
Step 2: Transaction Verification by Nodes
The transaction is broadcast to the peer-to-peer (P2P) network of nodes (computers).
Nodes validate:
- Authenticity: Is Alice’s signature valid?
- Funds: Does Alice have enough BTC?
- Fraud Check: Is this a double-spend attempt?
Bitcoin uses Script, a stack-based language, to verify signatures, and Ethereum nodes check gas fees to prioritize transactions. Imagine 10,000 accountants cross-checking your bank transfer. If 51% agree it’s valid, it proceeds.
Step 3: Creating a Block
Valid transactions are grouped into a block.
Each block includes:
- A header (timestamp, previous block’s hash).
- A merkle root (cryptographic summary of all transactions).
- A nonce (a random number used in mining, more on this later).
The merkle tree structure allows quick verification. Changing one transaction changes the root hash, invalidating the block.
Step 4: Consensus Mechanism (Mining/Validation)
Nodes compete to add the block to the chain using a consensus algorithm:
For Proof-of-Work (PoW):
- Miners solve a cryptographic puzzle (e.g., find a nonce that makes the block’s hash start with 0000).
- Requires massive computational power.
- First miner to solve it broadcasts the solution to the network.
For Proof-of-Stake (PoS):
- Validators are chosen based on their stake (coins held) and reputation.
- They validate blocks without energy-intensive computations.
Bitcoin’s PoW difficulty adjusts every 2,016 blocks to keep block time at ~10 minutes, and Ethereum’s PoS uses slashing to penalize malicious validators.
Step 5: Adding the Block to the Chain
- Once consensus is reached, the block is added to the blockchain.
- The block’s hash is generated and linked to the previous block’s hash, creating a chronological chain.
Changing a single transaction in Block #3 would alter its hash, breaking the link to Block #4, #5, etc., making tampering obvious.
Example: Bitcoin’s blockchain is ~500 GB tall, requiring unimaginable computational power to rewrite.
Step 6: Network-Wide Ledger Update
- Every node updates its copy of the blockchain to reflect the new block.
- The transaction is now permanently recorded and visible to all participants.
Example: In supply chains, this means a shipment’s origin, temperature logs, and delivery confirmations are globally auditable.
Step 7: Transaction Completion
- The receiver (Bob) gets the 1 BTC, and the network confirms the update.
- If it’s a smart contract, terms are auto-executed (e.g., releasing funds when conditions are met).
How AI Secures Decentralized Cybersecurity Using Blockchain
How blockchain enhances AI security systems lies in its ability to validate and log AI decisions immutably. The fusion of Artificial Intelligence and Blockchain technology is transforming the landscape of decentralized cybersecurity. Here’s how AI fortifies blockchain-based systems with intelligent, adaptive, and proactive defense strategies:
AI-Powered Threat Detection
AI algorithm fueled by machine learning, scan vast datasets from blockchain networks in real time. These blockchain-based AI threat detection systems act as intelligent sentinels, and their smart systems detect even the most subtle anomalies and suspicious behaviors, uncovering cyber threats that traditional rule-based methods often miss. Early detection = early defense.
Predictive Cybersecurity
This is where blockchain-based AI applications come into play. By distributing AI logic and data validation across nodes, we eliminate the need for a single authority.
Automated Incident Response
When a threat is flagged, AI in blockchain springs into action. It can autonomously isolate compromised nodes, block malicious activity, and initiate blockchain-based security protocols, drastically reducing response time and minimizing potential damage.
Smarter Data Protection
AI in blockchain enhancing data security with AI-powered systems by monitoring access patterns and deploying intelligent access controls. It also strengthens cryptographic key management and detects any attempts at data breaches or exfiltration in real-time.
Intelligent Vulnerability Management
With continuous scanning and self-learning capabilities, AI identifies known vulnerabilities and predicts zero-day exploits. This ensures systems remain patched, hardened, and always a step ahead of cybercriminals.
Tired of Centralized Vulnerabilities?
Discover decentralized cybersecurity powered by AI, a more resilient and robust approach to protection.
Blockchain Use Cases and Applications in Cybersecurity:
Blockchain’s decentralized, tamper-proof architecture is revolutionizing cybersecurity, offering innovative solutions to age-old vulnerabilities. Below, we explore key applications where blockchain app development is transforming digital defense mechanisms, complete with technical insights and real-world examples.
1. Immutable Data Logs
Blockchain’s tamper-proof ledger, combined with advanced blockchain AI services, ensures all activity logs remain unaltered and intelligently monitored. This creates transparent, verifiable records critical for audits, forensic analysis, and regulatory compliance.
2. Identity & Access Management (IAM)
Decentralized identity solutions powered by blockchain identity management eliminate centralized credential storage, drastically reducing the risks of phishing, identity theft, and unauthorized access. These solutions provide secure, user-controlled digital identities.
3. Secure DNS and DDoS Protection
Blockchain-based DNS systems, often integrated with blockchain IoT services, prevent DNS hijacking and mitigate DDoS attacks by distributing domain control across a decentralized network, thus removing vulnerable centralized points.
4. IoT Security
Securing IoT devices becomes robust with blockchain IoT services, which provide each device with a unique, verifiable identity. All interactions and transactions between devices are encrypted, recorded immutably, and protected from tampering or spoofing.
5. Cryptographic Key Management
Effective cryptographic key management is crucial in fields like crypto portfolio management. Blockchain facilitates secure key distribution and decentralized storage, making it significantly harder for attackers to compromise sensitive credentials and digital assets.
6. AI Model Integrity Verification
By leveraging blockchain AI services, organizations can verify that AI models used in cybersecurity remain untampered. Blockchain records ensure traceability of training data, model updates, and decision logs, enhancing trust in AI-powered defenses.
7. Threat Intelligence Sharing
Blockchain enables secure, real-time sharing of threat intelligence across decentralized networks. With blockchain AI services, this collaborative approach enhances the detection and mitigation of cyber threats by pooling community-driven insights.
Challenges and Solutions in Implementing AI and Blockchain for Decentralized Cybersecurity
Implementing AI and blockchain for decentralized cybersecurity holds incredible promise for robust, transparent, and proactive security. However, organizations often face critical challenges spanning technical, environmental, legal, and operational domains
1. Scalability:
One of the biggest technical limitations of blockchain is its relatively low transaction throughput compared to centralized systems. Public blockchains, essential for transparency and trust, can process only a limited number of transactions per second, which creates a scalability bottleneck especially when paired with data-intensive AI analytics.
Solution: Layer 2 scaling solutions such as state channels, sidechains, and rollups enable off-chain transaction processing while preserving security guarantees. Additionally, integrating AI-driven data prioritization helps filter and process only critical events on-chain, reducing unnecessary load and enhancing overall performance.
2. Energy Consumption:
Many blockchain networks, particularly those using Proof-of-Work (PoW) consensus mechanisms, consume massive amounts of energy, raising environmental concerns. When combined with the high computational requirements of AI models, this leads to significant energy consumption and carbon footprint.
Solution: Transitioning to more efficient consensus protocols like Proof-of-Stake (PoS) or Delegated Proof-of-Stake (DPoS) drastically reduces energy demands. Moreover, adopting AI optimization techniques such as model pruning and quantization minimizes computational overhead, making the combined system more sustainable.
3. Data Privacy:
AI’s power lies in data, but sensitive information such as user identity or transaction details must be protected. Blockchain’s transparent nature can conflict with data privacy, especially in blockchain AI services that require access to large datasets for threat analysis.
Solution: Employing privacy-enhancing technologies (PETs) such as zero-knowledge proofs (ZKPs) and homomorphic encryption allows AI models to analyze encrypted data without exposing sensitive details. Additionally, federated learning enables decentralized AI training on local data, preserving privacy while improving threat detection.
4. Interoperability:
Different blockchain platforms and AI systems often operate in isolation, creating silos that limit the seamless flow of data and security insights across networks.
Solution: Implementing interoperability protocols such as Polkadot, Cosmos, or Cross-Chain Bridges facilitates communication between disparate blockchains. Integrating APIs and middleware layers also allows blockchain AI services to interact smoothly with existing enterprise systems, enhancing unified cybersecurity coverage.
5. AI Model Bias:
Bias in AI models can lead to unfair or inaccurate cybersecurity decisions, potentially missing novel threats or generating false positives that disrupt legitimate activities.
Solution: Continuous model auditing and validation through blockchain AI services provide immutable logs of training data and decision points, enabling transparent bias detection. Combining this with diverse and representative datasets in federated learning frameworks helps develop fairer, more accurate AI-driven security solutions.
6. Integration Complexity:
Bringing together AI models and blockchain infrastructures involves complex integration challenges related to differing data formats, real-time processing needs, and secure communication.
Solution: Using modular architectures with well-defined APIs and microservices facilitates easier integration. Platforms offering combined blockchain AI services provide end-to-end solutions that abstract complexity and accelerate deployment.
7. Cost Barriers:
High costs related to blockchain transactions, AI computation, and infrastructure can hinder adoption, especially for small and medium enterprises looking to implement decentralized cybersecurity platforms.
Solution: Optimizing AI models for efficiency, adopting scalable blockchain solutions like private or consortium blockchains, and leveraging cloud-based blockchain AI services can significantly reduce costs. Additionally, pay-as-you-go pricing and open-source tools make advanced decentralized cybersecurity accessible to more organizations.
forms.
Secure Your Data the Smart Way!
AI analyzes threats before they strike, blockchain keeps your data safe, the intelligent future of security is here.
Real-World Applications of AI and Blockchain in Cybersecurity
The integration of AI and blockchain in decentralized cybersecurity is no longer theoretical, leading companies across industries are actively leveraging these technologies to secure sensitive data, prevent fraud, and enhance trust. Here’s a look at notable real-world examples:
1. Healthcare - Guardtime
2. Banking & Finance: IBM Blockchain with Watson AI
IBM combines its robust blockchain services with Watson AI to build intelligent fraud detection systems for financial institutions. Their solution analyzes transactional data on the blockchain to identify suspicious activities using machine learning models. A decentralized AI cybersecurity system using blockchain helps financial institutions detect fraud in real-time while maintaining transparent audit trails. This real-time monitoring enhances fraud prevention in payment networks and crypto portfolio management, reducing financial crime risks while ensuring compliance with global regulations.
3. Supply Chain: VeChain
VeChain uses blockchain IoT services paired with AI-driven analytics to provide end-to-end supply chain security. Blockchain-based supply chain management enables immutable tracking of goods and transactions, preventing counterfeiting and theft. AI models analyze sensor data from IoT devices to detect irregularities such as tampering or unauthorized access, ensuring product authenticity and transparency throughout the supply chain lifecycle.
4. IoT Networks: IOTA Foundation
IOTA leverages Distributed Ledger Technology (DLT) specially designed for IoT ecosystems, combined with AI-powered threat detection algorithms. Their framework enables autonomous IoT devices to communicate securely, detect cyberattacks, and react in real-time without centralized intervention. This approach reduces attack surfaces and protects connected devices across smart homes, industrial IoT, and autonomous vehicle networks.
Conclusion:
The future of cybersecurity with AI and blockchain is not only autonomous but also community-verified, transparent, and tamper-resistant. By merging AI’s predictive intelligence with blockchain’s tamper-proof architecture, businesses can create self-healing, decentralized defenses that outpace even the most sophisticated threats.
As cyberattacks grow in scale and complexity, relying on legacy systems is no longer an option. The future belongs to decentralized cybersecurity platforms where:
- AI detects anomalies in real time, learning from global threat patterns.
- Blockchain ensures trust through transparency and cryptographic security.
- Smart contracts execute defenses autonomously, slashing response times from hours to milliseconds.
The question isn’t if AI and blockchain will redefine cybersecurity, it’s how quickly you’ll adapt. Embrace this intelligent, decentralized future today, and turn cyber resilience into your greatest competitive advantage.
Act Now: Visit Blockchaintechs.io to explore custom AI-blockchain cybersecurity solutions tailored to your needs.
Ready to Build an Unbreakable Security Foundation?
The future of cybersecurity is decentralized and intelligent, let’s build your secure future together.
FAQs:
AI-powered systems detect threats in real-time while blockchain ensures data integrity, offering unmatched security, transparency, and automation.
Blockchain validates and stores AI decisions, creating transparent, tamper-proof logs that ensure accountability and trust.
Costs vary based on scope and complexity, typically ranging from $20,000 to $250,000+. Factors include integration, custom development, and compliance needs.
You can explore tailored services from Blockchaintechs.io—an affordable blockchain app development company with expertise in AI integrations.
The future of cybersecurity is heading toward intelligent, self-healing systems, where AI powers real-time threat detection and blockchain ensures trust, transparency, and decentralization. This powerful combination is revolutionizing traditional security models, making them more adaptive and resilient.
Partnering with the best blockchain technology company like Blockchaintechs.io empowers organizations to stay alert, agile, and future-ready, embracing next-gen cybersecurity frameworks that proactively defend against evolving digital threats.

